Metadata Explained: Why Your Message Content Isn't the Only Thing Being Tracked
In today's digital world, the content of your messages is just the tip of the information iceberg. Beneath the surface lies a vast network of data about your data – metadata. While you focus on crafting the perfect email, text message, or social media post, systems are silently collecting information about when you sent it, what device you used, your location, and much more.
.png)
Key Takeaways About Metadata
- Metadata reveals extensive context about your digital communications, often exposing more information than the actual content
- Every message you send contains dozens of hidden data points including timestamps, device information, and location data
- Organizations leverage metadata for security monitoring, behavioral analytics, personalization, and compliance purposes
- Government agencies and corporations collect metadata at massive scale for surveillance and profiling purposes
- Metadata persists longer than content and receives fewer legal protections despite its revealing nature
- Privacy-enhancing technologies like VPNs and encryption can help minimize your metadata footprint
Introduction to Metadata: The Hidden Information Layer
In today’s digital world, the content of your messages is just the tip of the information iceberg. Beneath the surface lies a vast network of data about your data—metadata. While you focus on crafting the perfect email, text message, or social media post, systems are silently collecting information about when you sent it, what device you used, your location, and much more.
Metadata serves as the structural framework that gives context to your content. It’s like the difference between having a photograph and having that same photograph with details about when it was taken, where, with what camera, and who was present. The image itself remains unchanged, but the surrounding information provides critical context that transforms how we understand and use it. This contextual layer often proves far more valuable to organizations than the content itself, because it can be analyzed to reveal patterns, relationships, and behaviors that would otherwise remain hidden.
As we rely more on digital platforms for communication, understanding metadata becomes not just a technical curiosity but a practical necessity. From privacy concerns to business intelligence, the information that surrounds your messages often proves just as valuable—sometimes more valuable—than the messages themselves. Every digital interaction generates a trail of metadata that can be collected, analyzed, and used for purposes ranging from service improvement to surveillance, often without your knowledge or consent.
In this guide, we’ll explore what metadata is, how it’s collected, why organizations track it, and what this means for your digital privacy and security—without burying you in technical jargon.
What Exactly Is Metadata? Defining the Invisible Framework
Metadata, at its core, is information about information. It’s the descriptive data that provides context, structure, and meaning to your primary content. When you send a message, the content might be “Let’s meet at 3 PM,” but the metadata includes when you sent it, from what device, your IP address, the recipient’s information, and potentially dozens of other data points. This structural information creates a framework around your content, enabling systems to process, categorize, and analyze it efficiently.
Types of Metadata in Digital Communications
Technical Metadata
Includes format specifications, file types, encoding methods, and technical parameters that define how data is structured and stored. This machine-readable information enables systems to properly process and display content across different platforms and applications.
Business Metadata
Encompasses definitions, rules, ownership information, and business context that helps users understand what the data means in practical terms. This layer translates technical information into business-relevant concepts that support decision-making and organizational processes.
Operational Metadata
Covers usage statistics, timestamps, performance metrics, and information about how and when data is being accessed and used. This dynamic layer provides insight into system performance, user behavior, and resource utilization patterns over time.
In messaging and communication platforms, metadata typically includes:
- Timestamps (created, sent, delivered, read)
- Sender/recipient identifiers (emails, phone numbers, account IDs)
- Device info (device type, OS, browser, language, screen settings)
- Location data (IP-based location, GPS if enabled, network location)
- Network details (carrier, Wi-Fi vs cellular, routing, signal strength)
- Message properties (size, format, encryption state, attachments)
- Interaction metrics (open status, reply time, forwarding, link clicks)
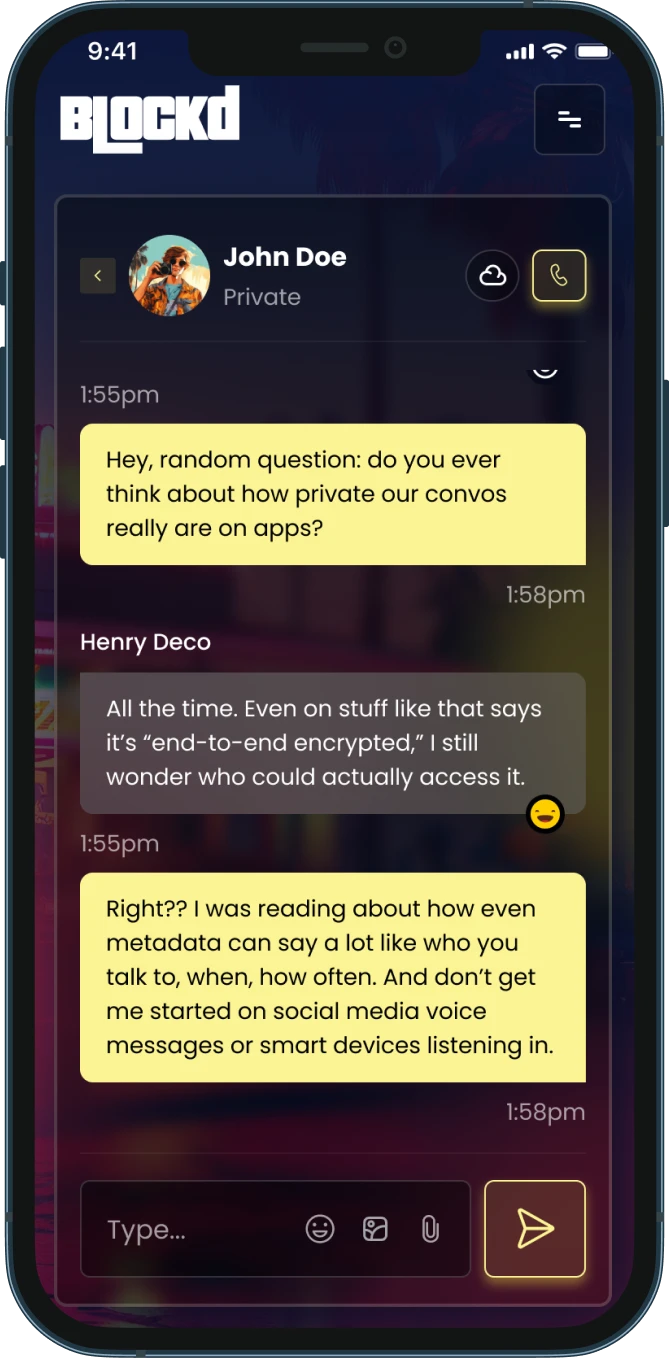
Unlike content, which you consciously create, metadata is often generated automatically and invisibly. It exists in structured formats that make it especially valuable for analysis: it can be sorted, filtered, and processed at scale by automated systems.
Also, the line between “content” and “metadata” is sometimes blurry. Subject lines, file names, tags, and categories often sit in the gray zone—content you create that also functions as descriptive context.
How Metadata Is Collected: The Silent Gathering Process
Metadata collection happens through technical mechanisms that operate mostly out of sight. These are baked into the architecture of modern communication systems.
Automated Collection at Message Creation
When you create a message, systems automatically record:
- Timestamp (often down to milliseconds)
- Account identifiers and authentication details
- App details (version, platform, configuration)
- Device information (model, OS, settings)
- Environmental preferences (timezone, language, accessibility settings)
Transmission and Network Metadata
As your message moves across networks, additional metadata is created:
- Routing information (IP addresses, hops, network path)
- Step-by-step transmission timestamps
- Encryption method indicators (cipher selection, handshake type)
- Server processing logs (queue position, processing state)
- Network performance metrics (latency, packet loss, bandwidth)
Reception and Interaction Tracking
When the recipient receives and interacts:
- Delivery timestamps
- Read receipts or “seen” timestamps
- Interaction data (replies, forwards, reactions, link clicks)
- Recipient device metadata
- Behavioral metrics (view time, engagement patterns)
Platform-Specific Collection Methods
Different platforms collect metadata through different layers:
- Email headers + SMTP/IMAP routing logs
- Messaging delivery/read receipt systems
- Social engagement tracking (impressions, shares, reactions)
- Video call telemetry (duration, quality, participant behavior)
- Cloud storage access logs (modification history, versioning)
- IoT device activity trails
This collection happens through APIs, cookies, tracking pixels, server logs, and background telemetry. And increasingly, machine learning systems infer additional metadata from patterns—even if the raw data was never explicitly collected.
Why Organizations Track Metadata: Beyond Simple Message Delivery
Organizations invest heavily in metadata because it’s structured, scalable, and extremely profitable or operationally useful.
Security and Fraud Prevention
- Detect unusual activity (account compromise, suspicious logins)
- Validate authentication chains
- Flag fraud patterns (location anomalies, behavior shifts)
- Reconstruct incidents in forensic investigations
- Correlate signals across systems to detect coordinated attacks
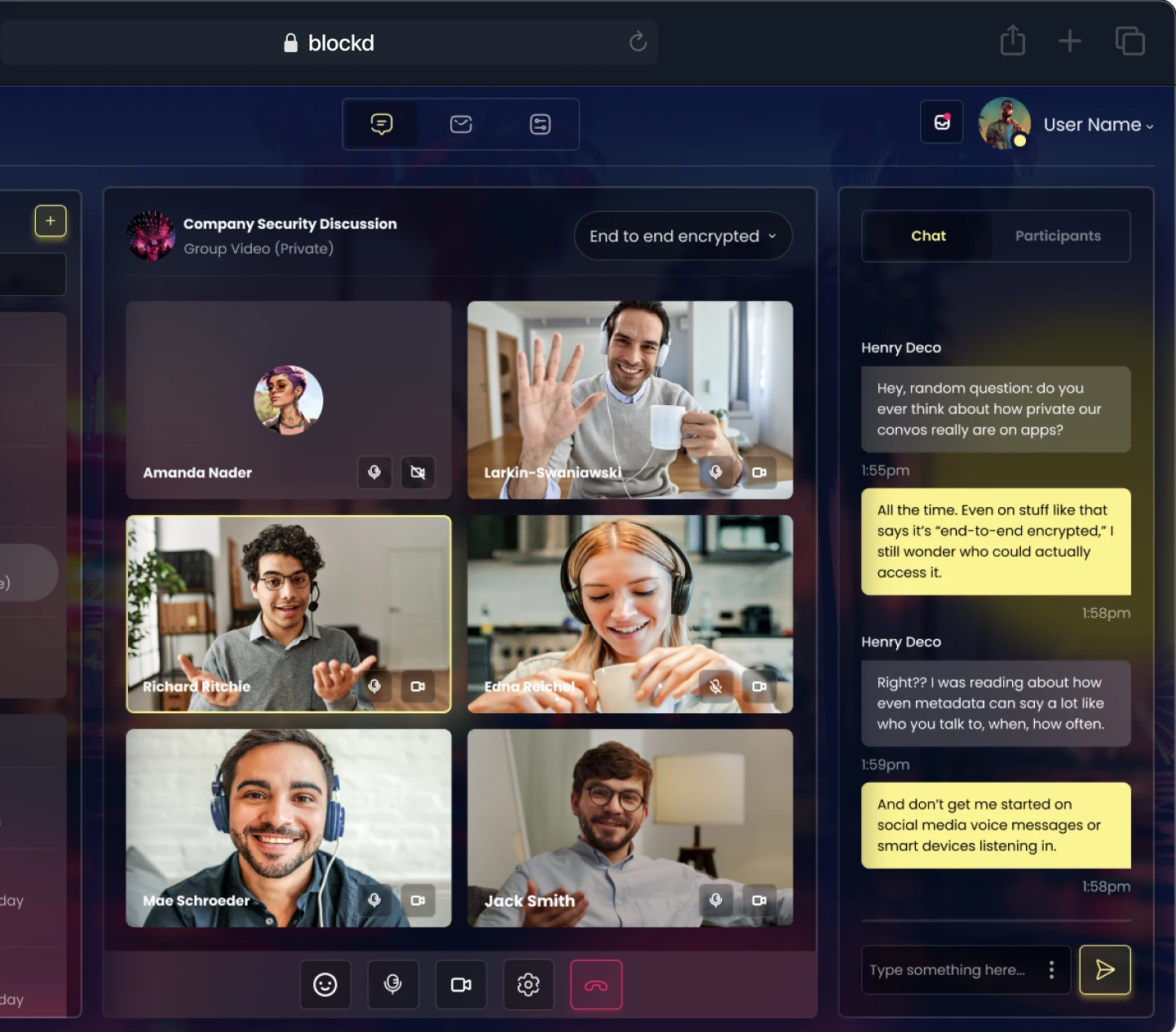
Business Intelligence and Analytics
- Measure usage patterns and capacity needs
- Identify performance bottlenecks
- Track feature adoption and engagement
- Detect trends early via behavioral patterns
- Derive strategic insights from large-scale interaction data
Metadata TypeBusiness ValuePrivacy ImpactCollection VisibilityTimestampsHighMediumLowLocation DataVery HighVery HighMediumDevice InformationMediumMediumLowInteraction MetricsHighMediumMediumNetwork DetailsMediumHighVery Low
User Experience Enhancement
- Prioritize messages based on relationship patterns
- Provide contextual features (“Sent from iPhone”)
- Power search and indexing systems
- Generate smart suggestions and predicted actions
- Adapt experiences for accessibility and personalization
Compliance and Legal Requirements
- Enforce retention schedules
- Maintain audit trails (who accessed what, when)
- Support legal discovery and chain-of-custody proof
- Meet industry-specific rules (healthcare, finance, education)
- Track cross-border data flows for regulatory compliance
Advertising and Monetization
This is where metadata becomes especially controversial:
- Build behavioral profiles (interests, intent, habits)
- Target ads based on patterns (even when content is encrypted)
- Measure ad effectiveness and conversions
- Track across platforms to build unified identity graphs
- Create “lookalike” audiences from metadata similarities
The key: metadata is often more valuable than content because it’s structured and easy to analyze at scale.
The Privacy Implications of Metadata Tracking
Metadata collection can create detailed profiles of individuals’ behaviors, preferences, and relationships—often far beyond what people expect.
The “Just Metadata” Misconception
Metadata can reveal:
- Your social and professional network
- Your daily movement patterns
- Your routines (sleep, work, exercise)
- Sensitive life changes (health, finances, relationships)
- Private connections you never intended to expose
Metadata and Mass Surveillance
- Social network mapping
- Pattern-of-life detection
- Lower legal barriers than content collection
- Target selection via anomaly detection
- Border and travel movement tracking
Corporate Surveillance and Profiling
- Cross-site tracking and ad targeting
- Data broker aggregation and resale
- Workplace monitoring
- Insurance risk scoring
- Financial behavior analysis for marketing and credit decisions
The Persistence Problem
Metadata often survives longer than content:
- Backups retain metadata even when content is deleted
- Metadata is valuable historically
- Once shared, it spreads across third parties
- Retention periods often exceed content retention
- Context outlives substance
Key Privacy Challenges with Metadata
- Invisibility: people don’t realize what’s collected
- Aggregation: small signals combine into sensitive patterns
- Persistence: data sticks around longer than expected
- Third-party sharing: spreads beyond the original collector
- Limited legal protection: metadata often treated as “less sensitive”
- Inference: analytics can derive hidden truths from “benign” data
Metadata becomes “digital exhaust”—a machine-readable trail that’s extremely useful for surveillance and profiling.
Protecting Your Metadata: Practical Steps for Individuals
Perfect metadata privacy is hard, but you can reduce exposure significantly.
Understand What’s Being Collected
- Read privacy policies focusing on “automatic collection” sections
- Audit app permissions (location, contacts, background refresh)
- Request your data exports when possible
- Use privacy tools to detect trackers and metadata leakage
Technical Protection Measures
- VPNs: mask IP and location from many services
- Tor: routes traffic through multiple relays to reduce traceability
- Privacy-focused messaging: minimize server-side metadata
- Privacy browsers: block trackers and fingerprinting
- Email aliases: reduce correlation across services
- Containers/profiles: isolate activities and reduce cross-context tracking
Behavioral Strategies
- Compartmentalize activities across separate identities/tools
- Limit permissions aggressively
- Avoid predictable communication patterns when it matters
- Don’t link accounts unnecessarily
- Delete old accounts and unused services to shrink your footprint
Advocacy and Collective Action
- Support privacy organizations pushing for stronger protections
- Participate in public policy consultations
- Choose products based on metadata practices
- Share knowledge with friends and teams
- Contribute to open-source privacy tooling if possible
Why “I Have Nothing to Hide” Is the Wrong Question
When people confront metadata tracking, a common reaction is: “I have nothing to hide, so why should I care?” That framing misses what’s actually at stake.
- Privacy is about power, not secrets
- Your data is rarely just about you
- Context can change overnight
- Profiles outlive your intentions
- You don’t control how the data is used
The real question isn’t “What do I have to hide?” but:
“Who should have the power to map, predict, and influence my life—and on what terms?”
How Blockd Treats Metadata Differently
Most messaging apps focus on encrypting content, but leave the metadata layer largely untouched. Blockd is built with the opposite mindset: treat metadata as sensitive, then design the system to reduce and control it.
Configurable Message Storage
- On-device only
- Temporary / ephemeral storage
- Blockd cloud
- Future user-owned ICP blockchain storage
Different conversations deserve different privacy levels—Blockd is designed to reflect that.
Choice of Network: Blockd Servers or the TOR Network
- Blockd servers: speed-first
- TOR routing: stronger anonymity via the real Tor network
You choose the mode based on your threat model, rather than accepting one default.
Account Security Built for a Post-Password World
- Passkeys: phishing-resistant, no reusable secrets
- Seed phrase recovery: user-controlled recovery, no weak reset flows
Advanced Cryptography and Secure Re-Encryption
- Quantum-resistant NaCl cryptography
- Re-encryption when you step away to narrow the attack window
Not Open Source — On Purpose (For Now)
Blockd is not currently open source, as a deliberate early-stage security choice:
- Harden core security model
- Iterate quickly on metadata reduction
- Avoid giving attackers a blueprint while evolving
Open-sourcing may be considered later, but it’s not short-term.
Clear Focus
Blockd focuses on configurable, privacy-first messaging:
- Minimize metadata needed to operate
- Control over storage and routing
- Modern authentication and recovery
- Build usability without unnecessary traces
Choosing Tools That Respect Your Metadata
When evaluating any messenger, ask:
- What metadata does it collect by default?
- Can I control storage location and retention?
- Can I route traffic through anonymity networks when needed?
- How modern and robust is the cryptography?
- Is the business model aligned with privacy, or monetization?
Most importantly: look for configurability. No single default fits every conversation.
Conclusion: Take Back Control of Your Digital Trail
Metadata isn’t a minor technical detail. It’s the backbone of how modern platforms understand, sort, and monetize your digital life. Even when your messages are encrypted, the who, when, where, and how often can be used to map your relationships, predict your behavior, and influence your decisions.
You can’t eliminate metadata entirely—but you can decide who collects it, how much they see, and how long they keep it. That starts with awareness, continues with better habits, and ultimately depends on tools built to minimize and protect metadata instead of exploiting it.
If you’re ready to move beyond “nothing to hide” and toward real control over your communications, explore how Blockd approaches metadata, encryption, and configurability at Blockd.ai. Your messages are only half the story—it’s time to protect the other half too.
.png)
.png)
.png)
.png)
.png)
.png)
.png)
.png)
.png)
.png)







_thumb.png)